Search for answers or browse our knowledge base.
-
POLICIES & PROCEDURES
-
TECHNOLOGY HOW-TO GUIDES
-
COMPUTING BEST PRACTICES
-
GENERAL TECHNICAL
-
NEWSLETTER ARCHIVES
Avoiding Phishing Attacks
Detecting Phishing Emails
Phishing is a fraudulent email that is designed to fool people into providing sensitive information such as user credentials, credit card numbers and banking information. Rather than exploiting technology, phishing attacks exploit human vulnerabilities. While phishing emails vary in format and content, there are a number of signs that will help you detect them and avoid any negative outcomes.
- Senders Name Should Match Email Address: Make sure that the sender’s name matches the email address. If the sender has a name you know but the email address doesn’t match, it’s likely a phishing message.
- Look for Odd Spelling Mistakes or Grammatical Errors: Typos aren’t unusual, but if you get an email claiming to be from a large company like Microsoft, Google, DocuSign, etc, grammatical errors are removed by professionals before sending. A lot of phishing attacks originate outside of the United States where English is often a second language and errors often indicate phishing.
- Do Not Give Out your Username or Password: No legitimate company will email you requesting your username and password. If you get an email asking you to send your username and password, it’s a phishing attack.
- Verify Website Before Clicking Link: Prior to clicking on a link, hover your mouse pointer over the link in the questionable email to view the actual destination address. An email may include a link that indicates a company like Microsoft, but if it’s a phishing attack, the link will take you to a website that has a web address that doesn’t match the organization.
- When in Doubt, Navigate to Website Manually: Be cautious when an email leads you to a website requesting your username and password. When in doubt, navigate to the website by manually entering the URL into your browser (do NOT click on the email link) on your own and then log in.
- Don’t Rush to Take Action: Be cautious of messages expressing a sense of urgency. This is used a tactic to trick the reader into acting quickly without spending time to consider the validity of the request.
- Take Time to Consider Message Requests: Be cautious of messages where an authority figure (the owner of the company or management) is making an unusual request such as a wire transfer or the purchase of a gift card. These type of messages often indicate phishing.
- If You Aren’t Expecting It, Question It: If you aren’t expecting an encrypted or secured document from someone, call them on the phone to verify that they sent it. The hardest attack to detect is one that comes from an already compromised email account belonging to an associate or coworker. In the case of targeted phishing attacks, attackers may review recent emails in the compromised account to create a highly customized attack. Points 6-8 are all very important when detecting these kinds of attacks, as unusual requests are typically the best indicator.
Taking Action
Mark as Spam & Delete: If you’re certain that the email is phishing, click on “Click here to mark this message as spam” at the bottom of the message to report it to the DTS SecureMail Anti-Spam service. After you’ve marked it as spam, simply delete it.
If Unsure, Forward to DTS: If you’re unsure if the message you have received is phishing, forward it to [email protected] and we’ll advise you on the validity of the email. Your office and patient security is always a top priority at DTS and we’re here to help!
Phishing Email Example
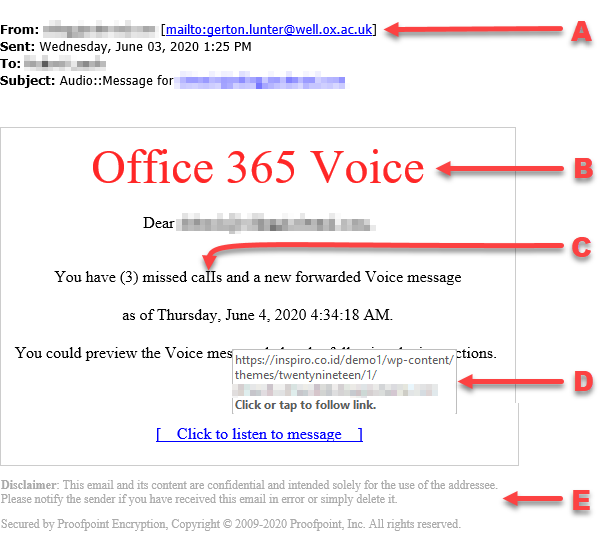
A. The name of the sender is familiar, however the actual email address is unknown. This is the first indication that there is a problem.
B. In this case, the service indicated in the email is not one that is in use at the office. If you don’t recognize the name of the product or service indicated in the message, don’t click any links or follow any instructions in the email.
C. This message, supposedly for a Microsoft service, has typographical errors, as capital I’s are used instead of lowercase L’s. These kind of errors are not generally found in legitimate business email.
D. Placing the mouse over a link in the message reveals the true address, which does not match the supposed sender of the email or the service. In this case, the link should reflect a “Microsoft” website address.
E. Often times, phishing emails will contain legitimate language, including links to other services.
